Real-Time Container Tracking Detects Tampering and Cargo Theft
Container tracking in ports and terminals is gaining progressively greater importance, with new use cases. In this article, we will present a use case for Security that some of our end clients are adopting, beyond traditional OCR systems that record container entries and exits by road, rail, or crane movement.
Scalable and tamper-proof technology
The container code is a globally unique identifier, designed in 1969 by the BIC (Bureau International des Containers) and subsequently standardized since 1972 by the ISO (International Organization for Standardization). It has the distinctive feature of being visible on all sides of the container with a standard format and position. This makes it a central element on which to base its traceability or tracking.
Alternatives, such as placing labels, tags, or devices of different technologies on each container, not only present a significant cost as they scale, but also involve complexity in terms of standardization, and are more sensitive to tampering. However, the container code is unique, global, and readable from all its sides (e.g., in case one side presents problems: dirt, damage, erasure, painting, etc.). Additionally, a single camera can read as many codes as containers passing in front of it, which implies instant scalability.
Thus, the base technology chosen for large-scale container tracking is computer vision. And solutions like AllRead’s make the difference in this field. On one hand, due to their ability to maintain extremely high reading accuracy rates (values around 98% or higher for containers). On the other hand, due to the lack of dependence on specific hardware, combined with great flexibility regarding installation infrastructure. That is, the necessary cameras can be installed according to internal regulations, choosing the models that best fit space constraints or a specific location. All of this makes it possible to place cameras in discreet, protected, and convenient locations.
Containers in motion: the vulnerable link
There is growing interest from terminals and port authorities in having traceability of containers while they are in their own facilities. This interest increases during moments when containers are moving within the terminal carried by trucks or internal tractors. It has been identified that during these movements containers are more exposed to possible tampering.
In this regard, it is worth remembering that the rip-off method presents one of the main mechanisms for adulterating container cargo for criminal purposes. Basically, it consists of opening the container after the cargo inspection at origin, to introduce illegal or undeclared products in a “parasitic” way. The same irregular opening operation is performed at destination, to extract the products before the relevant cargo inspection.
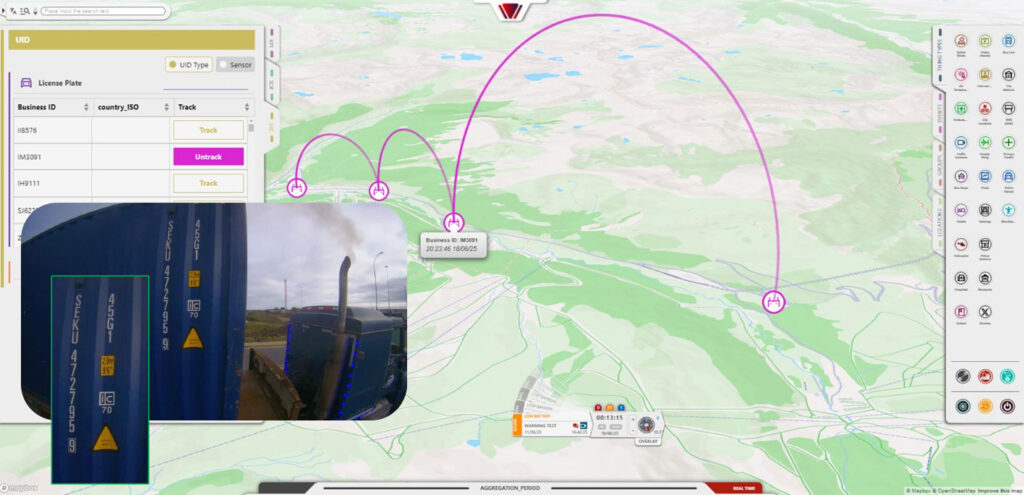
Therefore, in addition to monitoring and surveilling areas where containers are stored, such as the yard or depots, it is vital to control their movements inside the port and, related to this, know their travel times. Detecting in real-time abnormally long times or improper stops of trucks transporting containers will allow investigating and discovering the origin of such events.
From detection to action: the alert system
The control idea is simple: create control points throughout the port or terminal, especially on main travel axes, at intersections of circulation routes, at entrances or exits of depots or storage subareas, etc., with the objective of covering the main passage and movement zones.
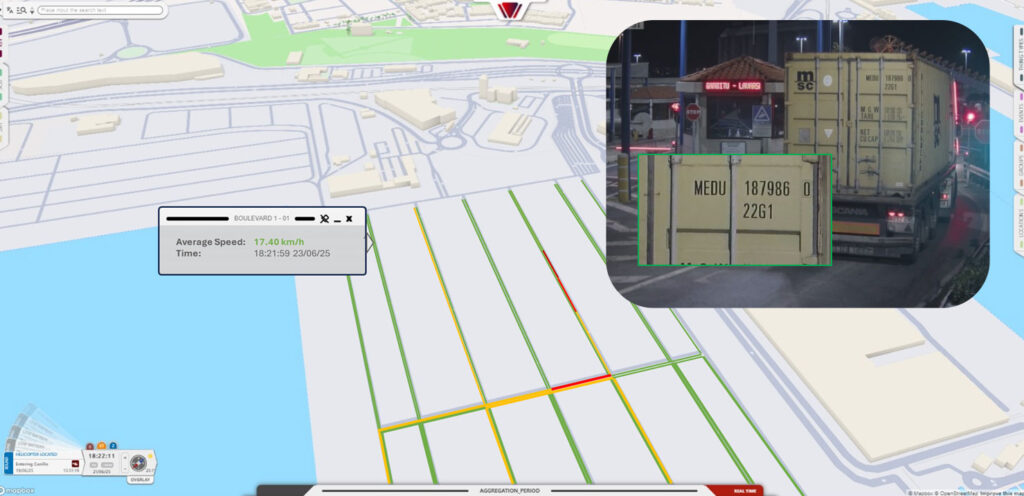
These control points will be equipped with one or more cameras from which to automatically and in real-time read the codes of containers passing in front, carried by trucks or internal tractors. Each of these readings will have other data associated with the container code, such as GPS position, timestamp (exact moment of reading), or an evidence image.
The computer vision solution will deliver each reading in real-time to the monitoring and management platform chosen by the client. This type of platform will be responsible for processing and presenting the information. On one hand, calculating travel times from the timestamps of each reading of the same container. On the other hand, comparing such times with thresholds or normalized values to detect possible anomalies. Anomalies will then be presented as alerts and these will be handled according to operational procedures.
An abnormally high time may be due to a real security event, but also to slow traffic in the terminal or a mechanical breakdown. Moreover, these platforms can use the received data for a second purpose. Using the accumulated historical movement data, it will be possible to create the traffic map in the terminal, defining what is “normal” in travel times. It is possible to correlate it with specific events, such as the arrival of a ship or weather events. So that this historical data can also help predict behaviors.
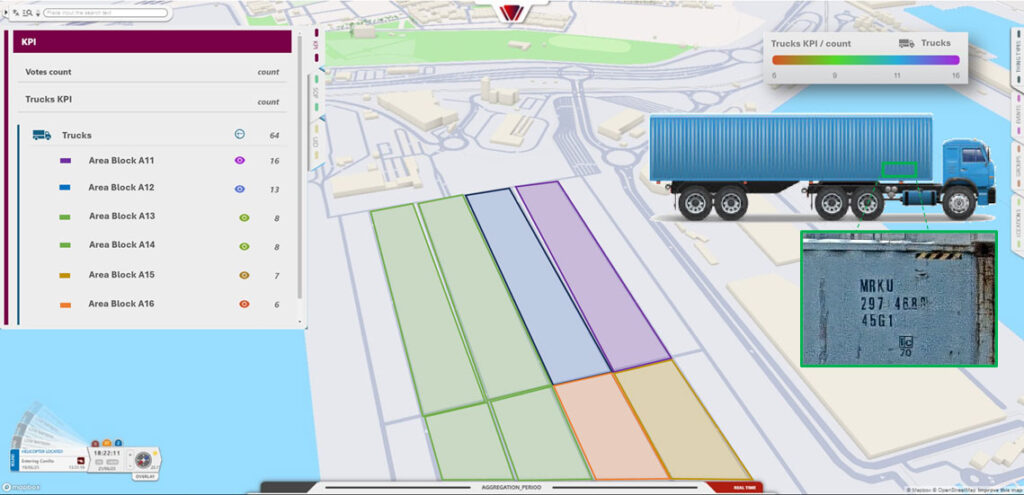
Operational optimization with the same infrastructure
The same container tracking presented for the purpose of supporting Security in the port or terminal can be used for other purposes, such as a boost to automation.
That is, the internal and precise tracking of containers can be replicated in the tracking of the terminal’s internal trucks or tractors, whose ID will become the license plate or code that the terminal assigns them and that they usually carry visible.
The automation of cranes and operations will be especially favored if the systems are capable of detecting where vehicles are at each moment, and their (estimated) arrival times to the positions assigned to leave or pick up a container. We will not go in deep, as this is not the purpose of this particular article.
The Future of Port Security
The container code, as a global unique identifier, standardized and always visible, opens a unique opportunity for its use by tracking applications based on computer vision. This approach makes fraud or tampering difficult, is more versatile, fully scalable, and achieves higher accuracy than other technological options.
There are already solutions in the market that allow for immediate implementation. For example, AllRead’s container reading model is highly reliable, well-tested, and offers a business model to make these projects totally viable. AllRead’s collaboration with solution partners also allows to provide a turnkey solution for maximizing the value of extracted data, from real-time anomaly detection to being able to build intelligence over time.
With all of this, ports and terminals will have better supervision of the assets they handle, increasing the efficiency and safety of their own workers.